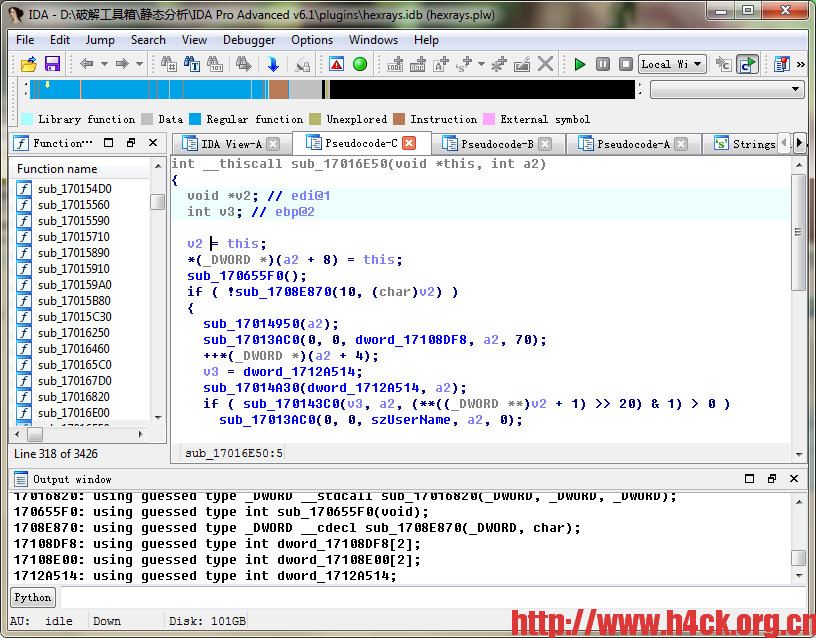
554748: push ebp
554749: mov ebp, esp
55474b: add esp, 0xfffffff8
55474e: push ebx
55474f: push esi
554750: push edi
554751: xor ebx, ebx
554753: mov [ebp + 0xf8]:32, ebx
554756: mov [ebp + 0xfc]:32, ecx
554759: mov edi, edx
55475b: mov ebx, eax
55475d: mov esi, [ebp + 0x8]:32
554760: xor eax, eax
554762: push ebp
554763: push 0x5548f6
554768: push [eax]:32
55476b: mov [eax]:32, esp
55476e: cmp esi, [ebp + 0xfc]:32
554771: jl 0x55477b
554773: cmp esi, [ebx + 0x2a0]:32
554779: jge 0x55479c
55477b: lea edx, [ebp + 0xf8]:0
55477e: mov eax, [0x7d9a60]:32
554783: call 0x40d6c4
554788: mov ecx, [ebp + 0xf8]:32
55478b: mov dl, 0x1
55478d: mov eax, [0x48dc40]:32
554792: call 0x428b3c
554797: call 0x408cb0
55479c: cmp edi, [ebp + 0xfc]:32
55479f: jge 0x5547a4
5547a1: mov edi, [ebp + 0xfc]:32
5547a4: cmp esi, edi
5547a6: jge 0x5547aa
5547a8: mov edi, esi
5547aa: mov eax, [ebx + 0x298]:32
5547b0: cmp eax, [ebp + 0xfc]:32
5547b3: jnz 0x5547bd
5547b5: cmp esi, [ebx + 0x29c]:32
5547bb: jz 0x5547f9
5547bd: mov eax, [ebp + 0xfc]:32
5547c0: mov [ebx + 0x298]:32, eax
5547c6: mov [ebx + 0x29c]:32, esi
5547cc: mov eax, ebx
5547ce: call 0x53bd64
5547d3: test al, al
5547d5: jz 0x5547f9
5547d7: cmp edi, [ebx + 0x294]:32
5547dd: setz al
5547e0: neg al
5547e2: sbb eax, eax
5547e4: push eax
5547e5: push esi
5547e6: mov eax, [ebp + 0xfc]:32
5547e9: push eax
5547ea: push 0x2
5547ec: mov eax, ebx
5547ee: call 0x53b98c
5547f3: push eax
5547f4: call 0x412cdc
5547f9: cmp edi, [ebx + 0x294]:32
5547ff: jz 0x5548e0
554805: mov [ebx + 0x294]:32, edi
55480b: mov eax, ebx
55480d: call 0x53bd64
554812: test al, al
554814: jz 0x5548c9
55481a: call 0x5b0b48
55481f: mov edx, [eax]:32
554821: call [edx + 0x118]:32
554827: test al, 0x1
554829: jz 0x554886
55482b: mov eax, ebx
55482d: call 0x5546ec
554832: test al, al
554834: jz 0x554850
554836: push 0x0
554838: mov eax, [ebx + 0x294]:32
55483e: push eax
55483f: push 0x2
554841: mov eax, ebx
554843: call 0x53b98c
554848: push eax
554849: call 0x412cd4
55484e: jmp 0x55486e
554850: push 0x0
554852: mov eax, [ebx + 0x29c]:32
554858: sub eax, [ebx + 0x294]:32
55485e: push eax
55485f: push 0x2
554861: mov eax, ebx
554863: call 0x53b98c
554868: push eax
554869: call 0x412cd4
55486e: push 0x101
554873: push 0x0
554875: push 0x0
554877: mov eax, ebx
554879: call 0x53b98c
55487e: push eax
55487f: call 0x412bcc
554884: jmp 0x5548c9
554886: mov eax, ebx
554888: call 0x5546ec
55488d: test al, al
55488f: jz 0x5548ab
554891: push 0xff
554893: mov eax, [ebx + 0x294]:32
554899: push eax
55489a: push 0x2
55489c: mov eax, ebx
55489e: call 0x53b98c
5548a3: push eax
5548a4: call 0x412cd4
5548a9: jmp 0x5548c9
5548ab: push 0xff
5548ad: mov eax, [ebx + 0x29c]:32
5548b3: sub eax, [ebx + 0x294]:32
5548b9: push eax
5548ba: push 0x2
5548bc: mov eax, ebx
5548be: call 0x53b98c
5548c3: push eax
5548c4: call 0x412cd4
5548c9: mov dl, 0x1
5548cb: mov eax, ebx
5548cd: mov ecx, [eax]:32
5548cf: call [ecx + 0x80]:32
5548d5: mov eax, ebx
5548d7: mov si, 0xffad
5548db: call 0x407bc8
5548e0: xor eax, eax
5548e2: pop edx
5548e3: pop ecx
5548e4: pop ecx
5548e5: mov [eax]:32, edx
5548e8: push 0x5548fd
5548ed: lea eax, [ebp + 0xf8]:0
5548f0: call 0x4095e4
5548f5: ret
5548f6: jmp 0x408b0c
5548fb: jmp 0x5548ed
5548fd: pop edi
5548fe: pop esi
5548ff: pop ebx
554900: pop ecx
554901: pop ecx
554902: pop ebp
554903: ret 0x4 |